Da qualche tempo sulla stampa internazionale vengono riportate notizie di quella che è ritenuta la nuova strategia del jihadismo globale: l’impiego di attentatori suicidi che possiedono caratteristiche psicologiche e sociali particolari. Si tratta di individui, principalmente donne, sofferenti di disagi mentali, nonché adolescenti sottoposti ad una azione di plagio da parte della virulenta retorica qa’idista.
Rapiti nel Jebel Uweinat – by Marco Lombardi
La questione dei turisti europei rapiti in questi ultimi giorni di settembre in Egitto ha tenuto tutti con il fiato sospeso: l’incertezza degli autori del rapimento, l’incertezza delle mosse diplomatiche in atto e il fascino dei luoghi lontani ha mobilitato, ha incuriosito e interessato. Cerchiamo di capire cosa è successo e dove… aggiungendo qualche considerazione.
Israele si gioca il tutto per tutto – by Giovanni Radini
Mazal tov signora Livni! Con la vittoria ottenuta nelle primarie di Kadima e le successive dimissioni di Olmert, sta al Ministro degli Esteri israeliano, Tzipi Livni, far uscire il Paese dalla ennesima crisi politica e formare un nuovo governo, capace di mantenere aperto il dialogo con i palestinesi, sulla base dei buoni propostiti espressi al summit di Annapolis nel novembre 2007.
Buldozer, ruspe e terroristi – by Marco Lombardi
Le Brigate degli uomini liberi della Galilea, Martiri di Imad Mughniyeh’ tornano a colpire: a marzo 2008 rivendicarono l’attacco di un terrorista solitario alla scuola rabbinica di Gerusalemme di Kyriat Moshe. Era la prima volta che compariva il nome del gruppo Kataeb Ahrar al-Jalil (Brigata degli uomini liberi della Galilea) – Gruppo del martire Imad Mughniye’ e i martiri di Gaza: ispirati a Imad capo militare degli sciti libanesi ucciso il 12 febbraio a Damasco nell’esplosione di un’auto bomba.
Dialogo con Aso Hunar, alto membro del partito Pjak – by Hamed N.
Hunar: noi non abbiamo fatto guerra alla Turchia, ma ultimamente è stata la Turchia che ci ha attaccato con gli elicotteri uccidendo sei guerriglieri dell’ufficio d’informazione. Alcuni giorni fa il capo delle forze armate turche Urkar Bashbug, ha dichiarato che vi sono accordi militari segreti con l’Iran per una collaborazione contro il Pjak (Partito della Libertà del Kurdistan) e il Pkk. Infatti, Hunar ribadisce che la Turchia sta formando le forze iraniane contro la guerriglia, perché le tecniche militari iraniane per questo tipo di guerra sono ancora di basso livello: è per questo che la Turchia ha messo a disposizione degli iraniani la propria esperienza.
Libano: fatto il Presidente ora serve il Governo – by Giovani Radini
Una cosa ci dicono gli scontri nella Valle della Bekaa e a Tripoli degli ultimi giorni: che la stabilità politica in Libano è solo di facciata. Si era pensato, esagerando con l’ottimismo, che l’elezione di Michel Suleiman a Presidente della Repubblica potesse fare da traino per la normalizzazione del Paese. Si era sperato che l’accordo di Doha chiudesse l’anno e mezzo di crisi e segnasse il principio della fine delle violenze. Invece i fatti di questi giorni ci portano a una realtà dai nodi ben più intricati.
La pace in Medio Oriente dipende da Olmert e lui da una sentenza – by Giovanni Radini
Tutto dipende da Olmert. O meglio dai numeri di cui dispone il suo governo alla Knesset e dalle decisioni della magistratura israeliana. Dopo il summit di Annapolis, a novembre 2007, si era detto che il 2008 sarebbe stato “l’anno della pace” per israeliani e palestinesi. Ancora oggi però di questo obiettivo non si vedono i risultati. Il processo di pace in Medio Oriente sta vivendo una fase di impasse. Certo, l’elezione di Michel Suleyman e l’apparente riapertura del dialogo tra Israele e Siria, in merito al “nodo Golan”, risultano indiscutibilmente in controtendenza alla situazione generale. Tuttavia è l’auspicato dialogo israelo-palestinese il cuore del problema. E questo ristagna non soltanto per le avversioni dei “falchi” di ambo le parti a raggiungere un compromesso. Ma soprattutto perché è schiavo della debolezza del governo israeliano. Il processo di pace quindi non va avanti per un motivo essenzialmente a sé estraneo.
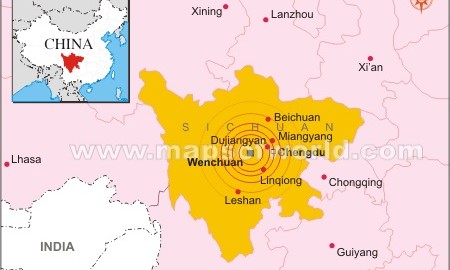
Sichuan (Cina): terremoto del 12 maggio 2008 – by Barbara Lucini
Il 12 maggio 2008 alle ore 14.28 (ora locale), la provincia cinese sud-occidentale del Sichuan[1] viene sconvolta da un forte terremoto di 7,8 gradi della scala Richter. Per l’intensità e la forza scaturita è stato classificato fra i terremoti più forti dal 1976. Il Sichuan è una regione molto estesa della Cina, ma soprattutto piuttosto popolata. La sua estensione territoriale uguaglia la Spagna, ma gli abitanti presenti sono il doppio ed appartengono a 53 etnie diverse; l’epicentro del sisma è stato individuato nella contea di Wenchuan[2].
New Perspectives on Terrorism
“This special issue of the Journal of National Defense Studies comes from a conference in held in 2006 in Herzelia/Gelilot, at the Israel National Defence College. Principal organizers were Edna Erez and Pini Yehezkeally, with the assistance of Orit Shalev and Jay Albanese, who sought to bring together experts on terrorism from relevant countries to address the different legal, cultural, religious, and political dimensions of terrorism found among different locations and groups. The National Institute of Justice, the research arm of the U.S. Department of Justice, co-sponsored the conference, and participated in the coediting of this issue. The findings and conclusions of the research reported here are those of the authors and do not necessarily reflect the official positions or policies of the U.S. Department of Justice.”
Read the whole special issue: New Perspectives on Terrorism
Tibet e Xinjiang sui media globali. Conflitti sul tetto del mondo, nello scacchiere del Grande Gioco – by Matteo Vergani
Dal Tibet allo Xinjiang
In questo gran frastuono mediatico sollevato dal caso tibetano, che ha conquistato dalle copertine dei tabloid ai monografici delle riviste di geopolitica, ogni tanto capita di sentir parlare dello Xinjiang: una regione a nord del Tibet, popolata da musulmani turcofoni (gli Uiguri), e ricca di risorse naturali. Anche lo Xinjiang, come il Tibet, è attraversato dalle istanze indipendentiste degli autoctoni, e anche lo Xinjiang è stretto dalla morsa di ferro della repressione cinese. Tuttavia tra i due casi esistono molte differenze.
Nuova intervista a Murad Karayilan (PKK) – by Hamed N.
Quale è l’obbiettivo della Turchia in questa offensiva militare nel sud del Kurdistan? È per fare pressione sul governo della regione e la questione della città di Kirkuk?
When the dust settles… Law and Order in peace support operations- by Pascal Carlucci
After a peace agreement is signed the international community has to transform diplomacy or military intervention into a political effort aimed at maintaining peace, and make it durable and fair for all parties involved. This requires a variety of engagements, not simply military and humanitarian. Projecting a post-conflict situation into durable peace requires first of all the re-establishment of public order and the rule of law.
Law and order in post-conflict societies is important for two main reasons. The first reason answers to a human security approach, which means providing the victims of conflict with a secure environment that, will protect them from being subjected to major violations of their fundamental rights. The second reason answers to a general requirement of democracy: the functioning and security of institutions. Institutions cannot work if they are under constant threat. The peace-building efforts in Afghanistan and Iraq are showing us the hurdle of enforcing the law with threatened institutions. The most delicate security post-conflict security problem is to free new-born democratic institutions from fear and aggression
Read the whole paper: When the dust settles…